
When you delete a file in Windows, only the reference to the file is removed from the file system table. The file still exists on disk until other data overwrites it, leaving it vulnerable to recovery.
There are many tools available out there that allow you to securely delete files so they cannot be recovered. This article provides a summary of some of the free tools available out there, many of which are portable, allowing you to securely delete files you may temporarily save to public computers.
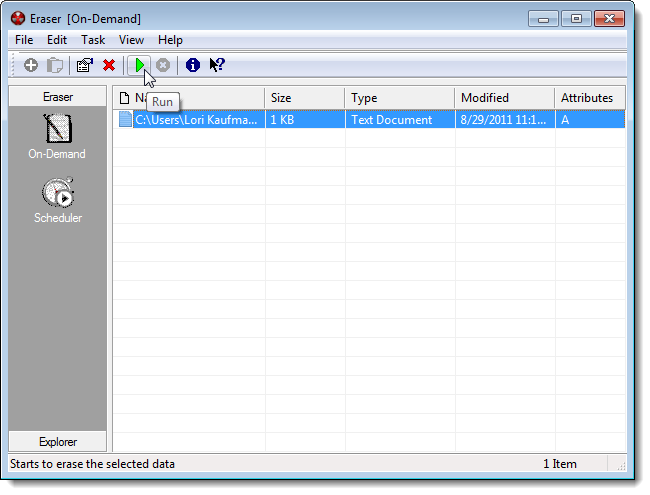
Eraser
Eraser makes it very easy to securely delete files, folders, or both. It overwrites the files being deleted with random data. There are several options for the number of times the files being deleted are overwritten with random data, including two versions of the US DoD 5220.22-M standard (3-pass and 7-pass) and the Gutmann method, which overwrites the file with random data 35 times.
You can immediately delete files and folders using the On-Demand interface or schedule files and folders to be securely deleted at a specific time using the Scheduler.
Eraser comes in a version you can install, which also allows you to add an option to the Windows Explorer context menu to securely erase files within Explorer. You can also download a portable version of Eraser you can take with you on a USB flash drive to delete files you save on other computers.
Download the installable version of Eraser from eraser.heidi.ie or the portable version from PortableApps.com.
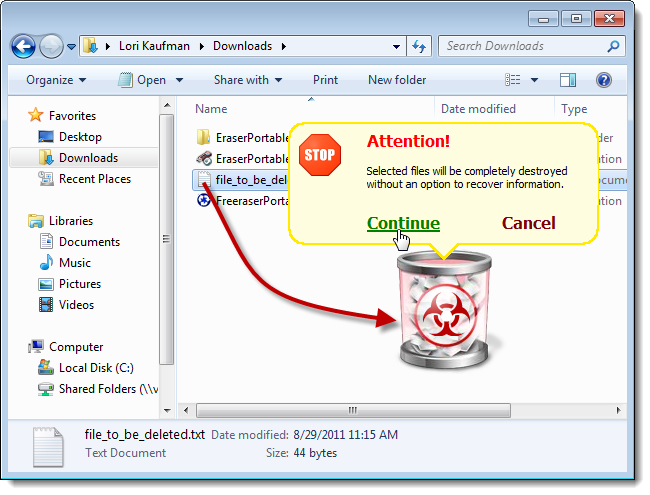
Freeraser
Freeraser is a free, portable tool that allows you to securely delete files using drag-and-drop. You can select to delete your files using a Fast method of filling the space with random data with one pass, using a Forced method that utilizes the DoD 5220.22M, 3-pass standard, or using the Ultimate, or Gutmann, method, deleting files by overwriting them with random data 35 times. Right-clicking on the Freeraser trash can displays a menu allowing you to manually select a file for deletion and to change the options for the program.
Download Freeraser from pendriveapps.com.
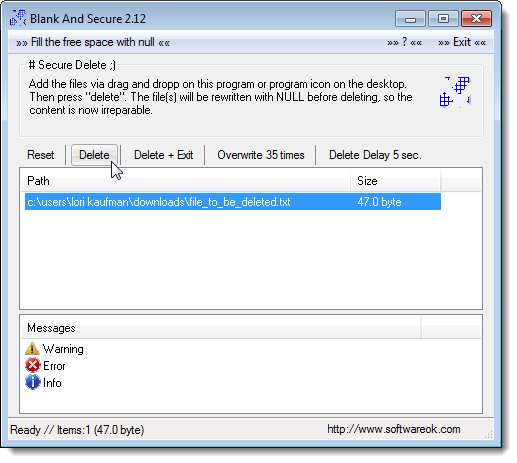
Blank And Secure
Blank And Secure is another portable drag-and-drop secure file deletion tool. Simply, drag-and-drop files or folders to be deleted onto the middle box on the Blank And Secure window. You can specify how many times the files are to be overwritten by zeros by clicking the Overwrite X times button and selecting an option. The deletion operation can be delayed up to 9 seconds using the Delete Delay X sec. button.
Download Blank And Secure from pendriveapps.com.
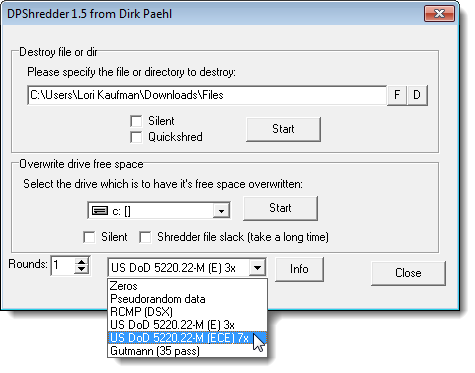
DP Shredder
DP Shredder is a portable, small program that allows you to securely delete files or directories and to overwrite the free space on a hard drive so files that were deleted previously without using secure methods cannot be recovered. You can easily select the method for deletion, which includes two US DoD-approved methods and the Gutmann method, and how many times (Rounds) the method will be applied.
Download DP Shredder from portablefreeware.com.
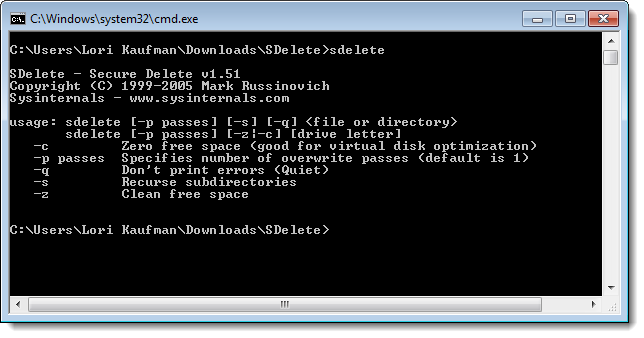
SDelete
SDelete is a command line tool allowing you to overwrite the free space on your hard disk so any previously deleted data becomes unrecoverable. It is portable and can be run from a USB flash drive in a command prompt window. To get help with how to use the command, type “sdelete” (without the quotes) at the command prompt and press Enter.
Download SDelete from technet.microsoft.com.
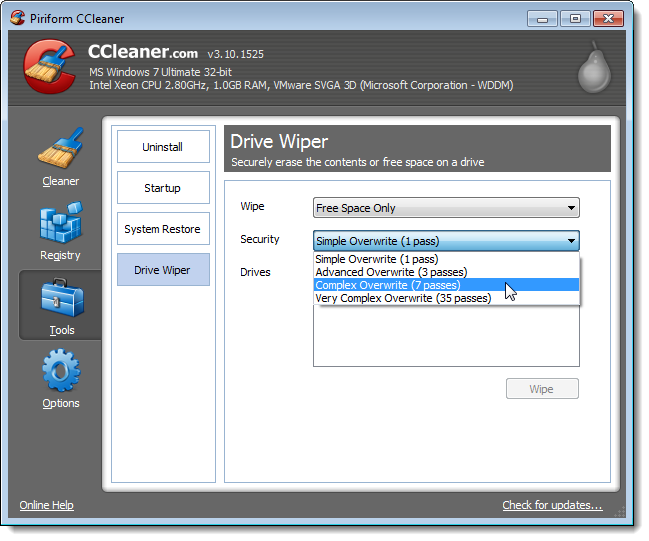
CCleaner
CCleaner is a program that removes unused, temporary files from your system, cleans up your internet history and cookies, contains a tool for cleaning the registry, and even allows you to clean up files from applications installed on your computer. The latest version offers a tool for wiping the free space on your hard drive. You can wipe the free space on a hard drive or the entire drive, securely deleting all data on the drive. There are four options for specifying how many times the data will be overwritten.
Download the installable version or the portable version of CCleaner from piriform.com.
A program for secure deletion of files is a useful addition to your software toolbox, especially if you use different computers, some of which may be public machines.
Cipher
We can accomplish this using Cipher with Windows PowerShell because while Cipher does not have a graphical user interface, it is still easy for anyone to use.
Press the Windows Key + S and begin typing PowerShell, then right-click on Windows PowerShell and Run as Administrator.
You can securely delete all free space on your hard drive by typing in cipher /w:C:.
This command will only securely wipe all free space that has deleted files. It will not touch any other files on your drive, so it’s safe. It is also the easiest and fastest command to wipe all deleted files securely.
If there’s one downside, Cipher is very slow. A large hard drive could take all night (or all day if you’re a vampire), and even secure deleting a single folder can take a half-hour or more.
For example, let’s say you wanted to wipe all deleted files from Documents securely.
In this case, we would type , where ‘Username’ is replaced with your username.
Cipher /w:C:UsersUsernameDocumentsIf you don’t know the full path, open File Explorer, This PC, Local Disk (C, and find the folder you want to wipe securely. In the screenshot below, we navigated to the %USERNAME% folder

That gave me C:\Users\%Username% in this case it’s “W”. You can use folder in here, or path or folder you like.
Now I type in followed by pressing Enter.
Cipher /w:C:Users\%USERNAME%\DocumentsSometimes Cipher will leave behind a folder and files called EFSTMPWP. What Is the EFSTMPWP Folder?.
That’s it!


















