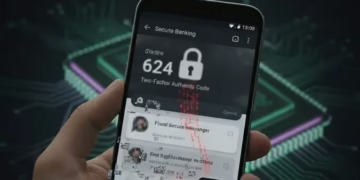
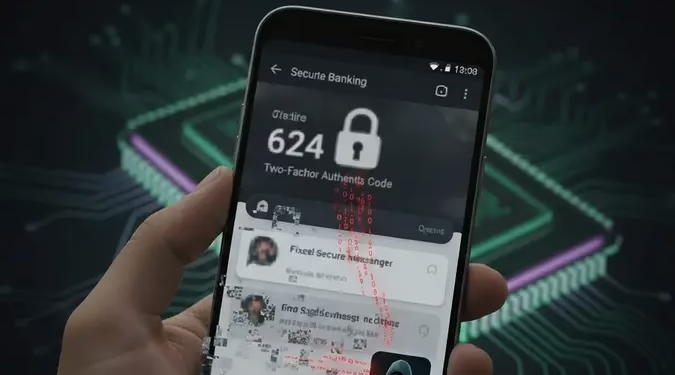
A new, high-severity vulnerability has been disclosed by a team of U.S. university researchers, and its implications go far beyond a typical software bug. Dubbed “Pixnapping,” this attack method, now tracked as CVE-2025-48561, can steal private on-screen data, including chat logs, financial information, and critical two-factor authentication (2FA) codes (Paccagnella, 2025).
The research, conducted by a team from UC Berkeley, University of Washington, UC San Diego, and Carnegie Mellon University, details how a malicious app can “read” a user’s screen without any special permissions.
At AckerWorx, we believe the true danger isn’t just the data theft; it’s that Pixnapping is an architectural flaw. This places it in a rare class of vulnerabilities that are historically the most difficult to fix and the most dangerous to ignore.
What is Pixnapping? (And Why It Bypasses Encryption)
Pixnapping is a sophisticated side-channel attack. It doesn’t exploit a simple coding mistake. Instead, it “weaponizes” legitimate Android APIs and a hardware side channel in the GPU to steal data (Malwarebytes, 2025).
Here’s the process:
- A user installs a malicious (but seemingly normal) application.
- The app uses built-in Android functions to infer what’s on the screen of another app (like Google Authenticator or your banking app).
- It leverages a GPU hardware flaw (dubbed “GPU.zip”) to measure the rendering time of pixels, which allows it to “read” the data.
- This data is then reconstructed, allowing the attacker to steal 2FA codes, private messages, and more, often in seconds.
This method completely bypasses all forms of software-level encryption. It doesn’t matter if your Signal messages are end-to-end encrypted; Pixnapping doesn’t intercept the data. It waits until the data is decrypted and displayed on your screen, and then reads it just as you would.
Real-World Parallels: Why Pixnapping is Not Just Another Bug
To understand the severity, it’s crucial to categorize this flaw correctly. This is not a simple buffer overflow. Pixnapping’s abuse of a legitimate feature to create a side channel places it in the same dangerous category as two of the most significant vulnerabilities of the last decade.
- Real-World Example 1: Spectre & Meltdown (2018): These infamous flaws didn’t “break” a CPU’s security. They abused a feature—speculative execution—to read data from protected memory. This was an architectural flaw in the very design of modern processors. The fix wasn’t a simple patch; it required a fundamental redesign of OS-level processes and even new CPU microcode, often at a cost to performance.
- Real-World Example 2: Rowhammer (2014): This is another hardware-level flaw where repeatedly “hammering” (accessing) a row of DRAM memory could cause bits to flip in an adjacent, protected row. Again, this wasn’t a bug in a program but an exploit of the physical design of the hardware itself.
Pixnapping operates on the same principle. It exploits a legitimate system process—rendering graphics—to read data it shouldn’t have access to. Like Spectre, the “flaw” is intertwined with the system’s intended design.
A Slow Patch Cycle: Evidence of an Architectural Flaw
The patching timeline, as reported by the researchers, is the strongest evidence of this flaw’s architectural nature.
- February 2025: Researchers disclose the vulnerability to Google.
- September 2025: Google releases an initial, partial patch.
- Post-September 2025: Researchers test the patch and find a workaround, proving the fix was incomplete.
- December 2025: A second, more comprehensive patch is planned.
A seven-month gap followed by an incomplete patch is not a sign of negligence; it’s a sign of extreme difficulty. Fixing an architectural flaw is complex. A simple patch can be bypassed because the root cause—the legitimate feature itself—remains. This slow, difficult remediation is exactly what the industry experienced with Spectre and Meltdown.
The Enterprise Risk: A Slow Security Supply Chain
For any organization, a 10-month or longer full patch cycle for CVE-2025-48561 is an unacceptable risk.
This incident exposes a significant vulnerability in the security supply chain. Enterprises managing fleets of Android devices—whether corporate-owned or in a BYOD (Bring Your Own Device) environment—are left exposed by this delay. It forces security teams into a reactive posture, relying on mitigation rather than remediation, and erodes trust in the platform’s ability to respond to critical threats.
How to Protect Your Organization from Pixnapping
While we await the definitive patch in December, AckerWorx advises all clients to treat this as an active threat. The primary attack vector is a malicious application.
- Audit Your Apps: All users, especially in an enterprise setting, must audit their installed applications. Scrutinize all permissions.
- Enforce MDM Policies: Use your Mobile Device Management (MDM) solution to enforce strict policies that prevent the “sideloading” of applications from untrusted, third-party sources.
- Prioritize the December Patch: The forthcoming December Android security patch must be treated as a critical-priority deployment for all Android devices in your organization.
- Educate Your Team: User education is the first line of defense. Reinforce security best practices and train employees to be suspicious of any app that seems to behave unusually (e.g., causing screen flickering or overlays).
Pixnapping is a significant reminder that the most dangerous threats often hide in plain sight, disguised as legitimate features.
References
- Malwarebytes (2025). Pixel-stealing “Pixnapping” attack targets Android devices. [Online]. Available at: https://www.malwarebytes.com/blog/news/2025/10/pixel-stealing-pixnapping-attack-targets-android-devices (Accessed: 27 October 2025).
- Paccagnella, R. (2025). Researchers uncover “Pixnapping,” a new class of Android attacks that can steal on-screen data in seconds. [Online]. Carnegie Mellon University CyLab. Available at: https://www.cylab.cmu.edu/news/2025/10/13-pixnapping.html (Accessed: 27 October 2025).
Pixnapping #Android #AndroidSecurity #Cybersecurity #Vulnerability #Malware #DataTheft #DataPrivacy #2FA #CVE #CVE202548561 #Google #GooglePixel #Samsung #Spectre #Meltdown #SideChannelAttack #InfoSec #CyberRisk #TechNews #AckerWorx #MobileSecurity #EnterpriseSecurity #BYOD